Most financial institutions have some type of two-factor authentication (2FA) now when you log into your account. You need something besides your username and password to access your account. The most common form of 2FA is a security code sent by text message to your phone.
Using 2FA is better than not using it, but different forms of 2FA aren’t created equal. Getting a security code by text message is the weakest form. When you have a choice, use a stronger form of 2FA.
The Weakest Link: Password Reset
Before banks and brokers implemented 2FA, the emphasis had been on the strength of your password — make it long and include mixed case letters, numbers, and symbols. With 2FA, the weakest link shifted to the password reset path. Criminals don’t bother cracking your password when they can just reset it.
As a drill, go through the “forgot password” process for your accounts and see which items are needed to reset your password. Those are the things you need to secure.
Google Voice for SMS
Some financial institutions send security codes by SMS text message to a mobile phone number on file. This is weak because a mobile phone number can be hijacked through SIM swapping. A criminal can reset your password and gain access to your accounts after they hijack your mobile phone number.
You should get a Google Voice number and only use that number for your financial accounts. A Google Voice number is less prone to getting hijacked. Install the Google Voice app on your phone and read the security codes in the Google Voice app. Don’t forward text messages sent to your Google Voice number.
Your Google Voice number is secure after you secure your Google account. Google supports using a hardware key (see the Yubikey section later in this post) or a mobile authenticator app.
Some places refuse to send security codes to Google Voice numbers. I would avoid using them if they send security codes by SMS text message but they don’t support Google Voice numbers. That’s one reason I closed my account with Ally Bank.
Secure Your Email
Some financial institutions send security codes and password resets by email. That means you must secure your email. If a criminal hacks into your email, they can get the security code and reset the password to your bank or brokerage accounts. See how an elderly couple lost $250,000 this way.
If you use Gmail, Google supports securing the account with a hardware key (see the Yubikey section later in this post) or a mobile authenticator app. Microsoft (Hotmail, Outlook.com), Apple iCloud, AOL, and Yahoo! also support securing email accounts with a hardware key or a mobile authenticator app.
Symantec VIP
Fidelity, Charles Schwab, and E*Trade support the free Symantec VIP mobile app on your phone. The app generates a six-digit security code that you use with your username and password.
A mobile app is more secure than text messages because it’s tied to a physical device, not to a phone number that can be hijacked remotely. However, you won’t be able to log in to your accounts if you lose your phone. Malware on your phone can also potentially read your security codes.
If you upgrade to a different phone, you can install the app on the new phone and migrate the credential ID from your old phone (requires app version 5.01 and above).
Hardware Token
Many people don’t know you can actually use a hardware token for Symantec VIP. The hardware token isn’t connected to the Internet, so malware on your phone can’t read it. You’re not taking the hardware token with you everywhere you go, and you won’t lose it if you lose your phone.

Some brokers provide a Symantec VIP hardware token for free if you ask them (Fidelity doesn’t). If your broker doesn’t provide it, you can buy one on your own at a minimal cost.
Go to the official Symantec VIP website. Click on “Buy Hardware Token” on the top right. The first link “Buy Security Token” sends you to the token sold on Amazon.

A Symantec VIP hardware token costs only $12.50 as I’m writing this. If this model is out of stock at Amazon, a different model is available on eBay for $10.
You can register the same token at Fidelity, Schwab, E*Trade, and anywhere else that also uses Symantec VIP.
Register Token with Fidelity
You must call Fidelity customer service to link the serial number of the security token to your login.
Fidelity requires separate tokens for separate logins. Get two tokens if you’re married and both of you have Fidelity accounts.
Yubikey
Vanguard supports Yubikey, which is a hardware key that you plug into a USB port on your computer or tap on your phone to read through NFC.
The least expensive Yubikey costs $25 or $29 on the manufacturer’s website depending on the type of USB port on your computer. The manufacturer also sells other models with more features at a higher price but the Security Key NFC series is sufficient for our purpose here.
You should register at least two Yubikeys with each account. The second key serves as a backup in case you lose one. If you’re married, get four Yubikeys — one primary key and one backup key for each spouse.
Keep your Yubikeys safely at home. Don’t put it on your keyring. Store your backup key(s) separately from your primary key(s).
Add Yubikey to Email Accounts
If you’d like to use two Yubikeys to secure your Google account (Gmail and Google Voice), follow the steps in Use a security key for 2-Step Verification from Google. Google sells Titan Security Keys but Yubikeys will work for both Google and Vanguard.
Microsoft, Apple iCloud, Yahoo, and AOL also support using Yubikeys.
Register Yubikey with Vanguard
To register your two Yubikeys with Vanguard, click on “Profile & account settings” on the top right after you log in.
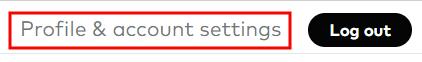
Click on the Security tab and then “Security key.”
Repeat the process to add your second key (and optionally the third and the fourth key). A married couple can register the same two Yubikeys with Vanguard for their separate logins. This way the two keys can work interchangeably for both logins.
Symantec VIP On Yubikey
For those who are more technically inclined, you can actually put a Symantec VIP credential on a Yubikey. It requires a more expensive version of Yubikey that has two “slots.”
This blog post by engineer Paul Sambolin gives details on putting Symantec VIP on a Yubikey for E*Trade:
After the Symantec VIP credential is put on a Yubikey, it works similarly for Fidelity and Charles Schwab.
This is too much work than it’s worth in my opinion because a Symantec VIP token is both inexpensive and straightforward. Go at it if you enjoy playing with technology.
Authenticator App
Fidelity, Morgan Stanley, T. Rowe Price, Betterment, Wealthfront, M1 Finance, and Robinhood all support authenticator apps for 2FA.
You link your login to an authenticator app on a mobile device, such as Google Authenticator, Microsoft Authenticator, or Authy. The authenticator app generates a six-digit code every 30 seconds.
The problem with an authenticator app is that it resides on your phone and you take your phone everywhere you go. It’s more prone to loss, theft, damage, software crash, or malware, whereas your hardware Yubikey or Symantec VIP token sits safely in your desk drawer. You can transfer the authenticator app from one phone to another when you upgrade your phone but you’ll have to learn how to do that.
2FA Directory
The website 2FA Direcory shows which 2FA methods are supported at each place. I go down a list of priorities: hardware > mobile authenticator app > SMS to Google Voice.
If a place supports hardware, I use hardware (Yubikey or Symantec VIP hardware token). If a place doesn’t support hardware but supports a mobile authenticator app, I use a mobile authenticator app (Google Authenticator, Microsoft Authenticator, or Authy). If a place supports neither hardware nor a mobile authenticator app, I give them my Google Voice number. If a place doesn’t send codes to Google Voice, I avoid them and go somewhere else when I have a choice.
Effect on Aggregator
Some people use an account aggregation service such as Mint, Quicken, or Empower (formerly Personal Capital) to pull information from multiple financial institutions into one place. Adding a hardware security token or authenticator app to your accounts doesn’t necessarily block the aggregators.
Aggregators usually get approval from financial institutions as a trusted third party for read-only access through a special channel. They don’t necessarily access your account through the same website you use to log in. I use Fidelity’s Full View powered by eMoney (see Fidelity Full View + Analysis: Track Your Portfolio Across All Accounts). It pulls information from Vanguard just fine after I added Yubikeys to my Vanguard accounts.
***
Buying security hardware costs more than using text messages or a mobile app, but the extra security and peace of mind are worth it. After I already spent the money on Yubikeys and a Symantec VIP token, I use them wherever I can.
Brokerage firms in general have better support for security hardware because they tend to deal with larger amounts of money. Most banks are still stuck at sending SMS text messages. It’s one reason that I closed my online savings account and favor using a money market fund now.
Learn the Nuts and Bolts
I put everything I use to manage my money in a book. My Financial Toolbox guides you to a clear course of action.


Phil says
Why you shouldn’t use Google Voice to get verification codes for Google Account
If you use Google Voice to get verification codes, you could lock yourself out of your account.
For example, if you sign out of your Google Voice app, you might need a verification code to get back in. But, because it’s sent to your Google Voice, you can’t get the code.
https://support.google.com/accounts/answer/185834?hl=en#:~:text=If%20you%20use%20Google%20Voice,code%20to%20get%20back%20in.
Kevin says
Google changed the defaults for security keys since you wrote this. They now want to use security keys to store passkeys, which serve as a “passwordless” form of authentication rather then a second verification step. I didn’t want to have to create and remember a new PIN, so I opted to use it as a second verification step. This required temporarily disabling the FIDO2 interface on the YubiKey before adding it to Google (which is how passkeys are stored), forcing Google to set it up as a second factor.
SSA says
Hi Kevin. I noticed google’s new requirement too. How did you disable/enable the FIDO2 interface?
Kevin says
I used the YubiKey Manager app to do this.
https://www.yubico.com/support/download/yubikey-manager/
Phil Ruggera says
When using security keys passwordless authentication is generally considered slightly more secure than 2FA. Here why:
1) Passwordless completely removes password-related risks like weak passwords, password reuse, or stolen passwords. 2FA still has the password as a potential weak point.
2) While both methods are phishing-resistant, passwordless eliminates the possibility of users entering their password on a fake site.
3) Passwordless authentication has fewer components that can be attacked, as there’s no password database to breach.
4) The easier login process of passwordless can lead to better security practices, as users are less likely to look for workarounds.
3) Passwordless aligns better with modern security principles and is more adaptable to emerging threats.
Kevin says
Thank you for the detailed reply! I hadn’t seen these benefits broken down so succinctly before, and they are compelling.
It looks like other services I’m planning to use my security key with support 2FA but not passkeys. Using 2FA feels like a smaller step in the right direction, but once more services support passkeys, they seem like the way to go.
Peter Sramka says
Two factor authentication is not just for accounts with passwords. You can have two factor authentication and password-less at the same time. That’s the way we do it at my job: No password plus two factor authentication.
Pat says
Do you have any advice regarding the recent security issues with Yubikey? Thank you.
Harry Sit says
Exploiting the security flaw requires physical access to your Yubikey and sophisticated equipment and skills. The risk is low if you’re not a high-value target and you don’t take your Yubikey with you everywhere. A random burglar of your home won’t know what to do with your Yubikey even if they steal it.
On the other hand, replacing your keys doesn’t cost that much to give you peace of mind, although you’ll need to register the replacement keys and remove the previous keys everywhere you used them.
Phil Ruggera says
If your YubiKey 5 firmware version is lower than 5.7 (or 5.7.2 for the Bio series and 2.4.0 for YubiHSM 2) best practice is to replace it. You can check your firmware version using the YubiKey Manager (start with ‘Run as administrator’ on Windows).
For those wanting 2FA with a hardware key, consider using the PIN feature. It improves security compared to not using a PIN. However, keep in mind that with FIDO2, if you enter the PIN incorrectly eight times, the key will lock, making it impossible to authenticate. The only option then is to reset the key to its default state (i.e., empty) and go through the setup process again from scratch.
Art says
Just a update on the VIP fob, it is ONLY sold on Amazon. It is now $16 each instead of $12 or so. There is about 17% of negative comments due to the fact that many of their batteries are either dead when ship or didn’t last as long as it supposes to (about 8 years), & can’t replace them.
I will just need to make sure I won’t lose my iPhone.
Harry Sit says
If you don’t want a fob, the Symantec VIP app on a laptop is a potential alternative. You take the laptop with you less frequently than you do with a phone. There’s less chance of loss or damage. Fidelity also supports any authenticator app now.
Pete says
I just logged on to my dormant Pentagon Federal Credit Union account. Penfed now allows Yubikeys perhaps making them more secure than most of the competition. I haven’t looked into it further to see if password reset issues still exist.
Eric says
I’ve set up a Yubikey with Vanguard but I’m concerned it is not fulfilling the promise.
The Vanguard mobile doesn’t work with the Yubikey. I believe it defaults to sms. So an account can be hacked bypassing the hardware key via the mobile app.
Harry Sit says
That’s why in addition to registering Yubikeys with Vanguard online, you give a Google Voice number to Vanguard and you use your Yubikeys to secure the Google account that owns the Google Voice number.
Jacob says
The training of Fidelity reps at the phone number for setting up their enhanced security options (800-544-6666) seems geared towards using the Symantec VIP authenticator app. They didn’t seem to have any idea what I was talking about when trying to register my Symantec hardware token with them. Apparently almost everyone uses the authenticator app, but I would really like to use the hardware token. Any suggestions on the best way to communicate this to them?
Harry Sit says
The token and the app work the same way. You don’t have to say what exactly you have. Just pretend you have the Symantec VIP app. That makes it easy for everyone. The rep only needs the identifier and the code. It doesn’t matter whether those come from the token or the app.
MIkeS says
I just spent 20 minutes talking to Fidelity support wanting more info on the Symantec VIP FOB versus the app. Said she needed to call the back office to get more info. She said they don’t support the FOB as it’s easy to loose. After more questioning she said I need to call Symantec and ask them if the FOB works at Fidelity. The more questions I asked the more she kept proving to me that she knew nothing about this stuff.
I mainly to find out that if I get a FOB can it be used for both mine and my wife’s accounts access.
Harry Sit says
A specific fob can be used only with one username. If you ask the rep to link it to a second username, they’ll get an error saying it’s already associated with another user. I guess the same goes with the ID from an app. Two users will need two fobs, two apps, or one fob and one app.
MikeS says
I decided to get a Yubi to better secure my non Fidelity accounts, mainly Amazon and Google. I’m a techy, recently retiring after a near 40 year career as a software developer. I am no security expert but over the years have dealt with a lot of security stuff.
I’m glad the Security Key NFC series was recommended above as I would have really blown a gasket trying to figure out which of the better than 20 different keys to choose from. The Yubi sight has a lot of information but not a bit it is all geared toward security experts.
I was a bit excited to receive my key but that excitement quickly faded. I first tried to follow the Yubi directions fro my Google account, they are out of date. Google has help in this area but I believe the same folks that wrote the Yubi documentation wrote the Google directions….they didn’t help much. I then tried to access via my phone and my phone would not read the key via NFC so I had to use it via USB. I finally got things setup but I am still able to login with just a password. I moved onto my Amazon account and quickly learn that the Yubi directions are for Amazon AWS not the Amazon sales site. I found directions at Amazon and again they are very poorly worded but finally got the key registered. I try to get in on my phone (Android) and it says NFC issue use the USB interface, I plug it in and we proceed for Amazon to ask for a PIN. I never setup a PIN anywhere. I moved onto ID.Me and found that was a very simple and easy process to add the Yubi, I was shocked here as they have been the least user friendly when I initially setup the account.
Time to get a support request and ask why NFC does not work and how I get by the PIN request. They were responsive but just pointed me at the article I had already read. I discovered at the end of one article I see they mention NFC does not work on the key until after it’s been plugged into USB at least once. Support said that Google Play has an issue and thats why Amazon does not work. Baffling as the NFC works just fine with the Yubi app.
All the above was a very condensed version of events from a few weeks back but I had many hours involved. Yubi said I could return the key for a refund but I have not. After reading more details in posts above I may retry my efforts after doing some more research on a day I have little to do.
I will say I have walked away from this so far stunned as to how difficult they have made it to simply require a physical key to provide access to your accounts. It’s like they really don’t want you to use them. Yubi will never get into the consumer market unless they provide some consumer support.
Peter Sramka says
I also just retired as a software developer. I got a Yubikey almost a year ago. I set it up with my Google account and my Apple ID account. Just like you, I ran into outdated instructions and all kinds of quirks and bugs. I spent a lot of time on it but eventually I got everything to work via trial and error. It was the exact opposite of user friendly.
Harry Sit says
The PIN is a PIN you set for the Yubikey. If you never set one before, you can set any PIN when you’re asked for a PIN the first time.
MikeS says
The PIN that Amazon wants is not the Yubikry PIN that I use to access the Yubikey in the Yubi app.
Randy says
A note re: Fidelity. You can use a YubiKey to generate a OTP for Fidelity and avoid the risks outlined in the article from using an authenticator app on a mobile phone. However, I don’t see a way to register both a primary and a backup YubiKey device with Fidelity for OTP purposes, so loss/failure of the primary YubiKey would require manual authentication with Fidelity followed by a reset of their 2FA settings.
Bill says
I called Fidelity on April 1st to set up. my Symantec VIP hard token.
They advised that support for that ended on March 26th 2025.
They are only supporting phone based soft tokens now.
Any ideas for a hard token? Thanks.
FredS says
“If you upgrade to a different phone, you can reinstall the app but the Symantec VIP credential ID can’t be transferred to your new phone. You’ll have to link a new credential ID to your login.”
This is not correct. You can in fact migrate the credential from one phone to another.
Harry Sit says
That was the case at the time I wrote the article. I see you can migrate the Symantec VIP credential now after app version 5.01.
Bruce says
They told me the same thing. I asked for them to make an exception. After checking they went ahead and implemented to VIP token. When the asked for the code they wanted something other the s/n on the token. Per another comment I asked them to use the s/n on the token starting with FT. They did and it worked. The next day when I called to implement my wife’s token they didn’t object but again, I had to ask them to use the s/n on the token starting with FT. Again, it worked.
Bruce says
I just called Fidelity to add the Symantec key to my account and was told that as of today they have stopped using Symantec. I asked for an exception and after waiting for the agent to talk to his supervisor he was able to take my key code (serial number) and it works. He tried to explain the issue and it sounded like it was an issue with customer service support but he really didn’t know. All I know, it is working. I also added Schwab, no problem on the website.
Harry Sit says
Fidelity started supporting generic authenticator apps a few months ago. It’s understandable that they’ll stop adding new users to Symantec, which is proprietary and it costs them money. Supporting generic authenticator apps gives customers a choice in which app(s) to use and where (mobile, desktop, cloud). I still use the Symantec hardware token but I’ll switch to an authenticator app if Fidelity stops supporting Symantec for existing users.
Bill says
Bruce, thanks for your report, but I tried the same thing using your verbage just now as a premium member and was denied a second time. I was told again that there is no support for any hard tokens and they don’t have their own.
They only support soft tokens or you can call customer service everytime and they will give you a code over the phone.
Thanks for your report.
Randy says
I don’t understand your question. You can use a YubiKey per my Feb 7 comment.
wilsonhammer says
You don’t need the Symantec App or hardware token. You can use any TOTP app you like for services that “require” symantec stuff.
https://www.reddit.com/r/personalfinance/comments/hvvuwl/using_google_auth_or_your_totp_app_of_choice_for/
Craig says
I logged into my Fidelity account this morning on my phone and a message popped up that I had to change to a new authenticator app as they were discontinuing support my Symantec VIP hardware token.
Can you comment on any other options for fidelity access with a physical hardware token? Thanks!
Pat says
Harry mentioned in previous post “ I still use the Symantec hardware token but I’ll switch to an authenticator app if Fidelity stops supporting Symantec for existing users.” . Is authenticator app better than 2 factor using Google phone?
Harry Sit says
An authenticator app is better than 2-factor codes sent to a Google Voice number because an authenticator app is purely based on time. It doesn’t require any network connection.
Harry Sit says
I’ve switched to Proton Authenticator on a desktop. It’s not a hardware token but it’s not on my phone that I take everywhere. You can also run it on an old phone or tablet that stays at home with WiFi off. That’s basically a hardware token with a larger screen.
https://proton.me/authenticator
Pat says
Thanks Harry, very helpful.